Security boundary is not formed by firewalls, routers, gateways or identity. It is only defined by your budget and the regulations you are subject to, if they exist. You cannot bend the regulations according to your comfort, and your budget may be directly affected by economics that is adepto ex imperium. Security is a game of boundaries and vulnerabilities.
The game is agonizing, compromised and prone to uncertainty.
In this condition, how might the state of security level be? More investment does not mean a higher level of security. Thereby, it is difficult to measure security level. What about maturity level, that some think it is strongly tied with security level, but depending on whom or according to what? Measuring security level is heavily based on controls and it can not go beyond an estimation. And all controls are also boundaries.
What about vulnerabilities? We cannot prevent vulnerabilities due to the eternality of the error-prone nature of human. May AI be with us! We can only patch them as long as we catch them. Boundaries can be disciplined under some circumstances. But boundaries are deterministic, and they are economics. So, when you evaluate the level, you need to take into account economics.
The Economics of Security
The economics of security can be explained by using economic theory and behavioural economics, not only through technical security itself. The connection regarding economics disciplines can be found in Ross Anderson’s paper in 2001(1). According to that, information insecurity mostly arises from perverse incentives rather than lacking solid boundaries. As he points out in his paper “many of the problems can be explained more clearly and convincingly using the language of microeconomics: network externalities, asymmetric information, moral hazard, adverse selection, liability dumping and the tragedy of the commons“.
There can be a reversible logic that many of the security problems arise due to misallocated costs in terms of responsibility and liability (Tyler Moore 2010)2. To solve the increasing security problems, policy and legislation must correlate with each other and coherently designate responsibilities/liabilities so that the stakeholders have an incentive/cause to undertake.
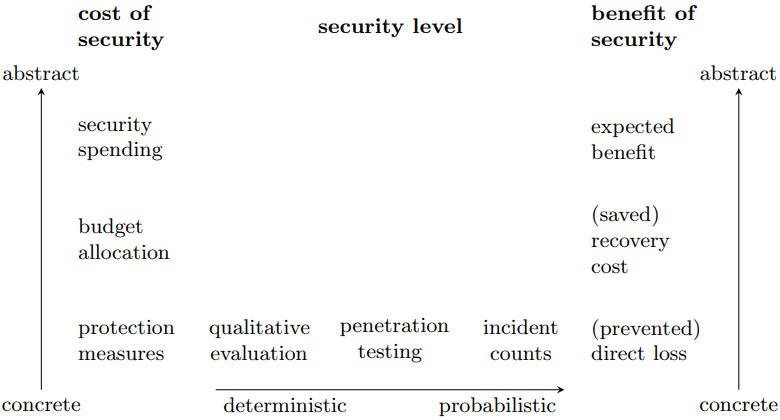
Measuring Security Level
When measuring security level, the related metrics consist of controls, vulnerabilities, incidents and prevented breaches/losses. And if we put these metrics on an axis, controls come first and reside on the far left side of the axis together with vulnerabilities on the right of it. En attendant, incidents and prevented losses sit on the right side of the axis.
<== controls || vulnerabilities || incidents || prevented losses ==>
Whereas controls and vulnerabilities are deterministic and action-driven, incidents and prevented breaches/losses are stochastic/probabilistic and event-driven. Your choices/products/assessments/level sways on the axis based on the related metrics’ weight distribution of them throughout the axis.
Looking at popular frameworks in practice, you see all control-based metrics and vulnerabilities are only addressed in terms of the controls needed to deal with them. They are steady-state. The most remarkable thing is that if they are developed by the security industry or security providers, most framework metrics mainly focus on controls and vulnerabilities. Why? That is because:
- controls are easy to measure.
- industry, vendors or security providers sells security solutions (easy to sell) which are controls.
- controls are only interested in implementation effort, not attack results or breaches.
- controls leave the risk of failure to its buyers.
Given these circumstances, incidents give more valuable feedback such as the determining how to allocate your resources efficiently, rather than controls. In the meantime, incidents are not easy to interpret or evaluate. Differentiating true signals from noise is cumbersome due to noncontrollable attacker movements and the other non-security factors. So, they need to be correlated or combined with controls and vulnerabilities metrics.
Whatever solution is applied or choice is made, as long as security threats are rated qualitatively and controls are evaluated prospectively according to emerging threats, more comprehensive results are gained and more stable grasp of security posture is maintained. Speaking repeatedly, whether security or security level is mentioned, this is a game in which the most important dynamic is economy in the name of seller-buyer, defender-attacker or boundaries-vulnerabilities.
Further Readings
- Ross Anderson: Why information security is hard – an economic perspective
- Tyler Moore: The economics of cybersecurity: Principles and policy options
- Rainer Böhme: Security Metrics and Security Investment Models
- Nicola Jentzsch: State-of-the-Art of the Economics of Cyber-Security and Privacy
- Ross Anderson and Tyler Moore: The Economics of Information Security
- Joseph J. Cordes: An Overview of the Economics of Cybersecurity and Cybersecurity Policy
- Ross Anderson’s Economics and Security Resource Page
- Economics of Security: Facing the Challenges